Managed Security Services: Empowering Businesses to Safeguard Their Digital Assets
As the threat landscape has continued to evolve, businesses require advanced and reliable security solutions to protect their digital assets. Managed Security Services (MSS) have emerged as a comprehensive solution for businesses seeking to enhance their cybersecurity posture.
The Role of Managed Security Service Providers (MSSP) in Cybersecurity
A Managed Security Service Provider (MSSP) is a third-party vendor that provides managed security services to businesses. Managed security service providers offer a suite of cybersecurity services, including threat detection and response, vulnerability assessment, compliance management, and security monitoring. By outsourcing their security needs to a managed security service provider, businesses can focus on their core competencies, while ensuring they have a reliable and effective security strategy in place.
Managed IT Security Ensures Comprehensive and Proactive Cybersecurity
In today's digital age, businesses face a growing number of cybersecurity threats that can compromise their valuable digital assets and disrupt their operations. To safeguard against these threats, businesses need a comprehensive IT security strategy that includes proactive threat detection, vulnerability assessment, and incident response. Managed IT security services have emerged as a critical solution for businesses seeking to enhance their cybersecurity posture. In this article, we will explore the benefits of managed IT security services and how they can help businesses safeguard their digital assets against potential security threats.
Understanding Managed IT Security
Managed IT security refers to the outsourcing of IT security services to a third-party vendor, known as a Managed Security Service Provider (MSSP). MSSPs offer a suite of cybersecurity services, including threat detection and response, vulnerability assessment, compliance management, and security monitoring. By outsourcing their IT security needs to an MSSP, businesses can focus on their core competencies, while ensuring they have a reliable and effective security strategy in place.
Managed IT Security Sheds Light on Cybersecurity Concerns
Managed IT Security Services offer several benefits for businesses, including:
-
Comprehensive Security Strategy: Managed IT Security Services provide a comprehensive security strategy that covers all aspects of the business's infrastructure. From threat detection to vulnerability assessment, the managed IT security service providers can help businesses identify and mitigate potential security risks, ensuring their digital assets are protected against potential cyber threats.
-
Cost-Effective Solution: Managed IT Security Services are a cost-effective solution for businesses seeking to enhance their cybersecurity posture. By outsourcing their security needs to a managed security service provider, businesses can avoid the costs associated with hiring and training an in-house security team.
-
Continuous Proactive Monitoring: Managed IT Security Services provide continuous 7x24 real-time monitoring of the business's infrastructure, ensuring potential security threats are identified and addressed in real-time. This proactive approach to cybersecurity helps businesses stay ahead of potential threats, reducing the likelihood of a security breach.
-
Regulatory Compliance: Managed Security Services can help businesses comply with regulatory requirements, such as GDPR, HIPAA, and PCI-DSS, by providing detailed reports of security activity and incident response.
-
Scalability: Managed Security Services are scalable, allowing businesses to adjust their security strategy as their needs evolve. Managed security service providers can provide customized solutions that meet the unique security needs of each business, ensuring their digital assets are protected against potential security threats.
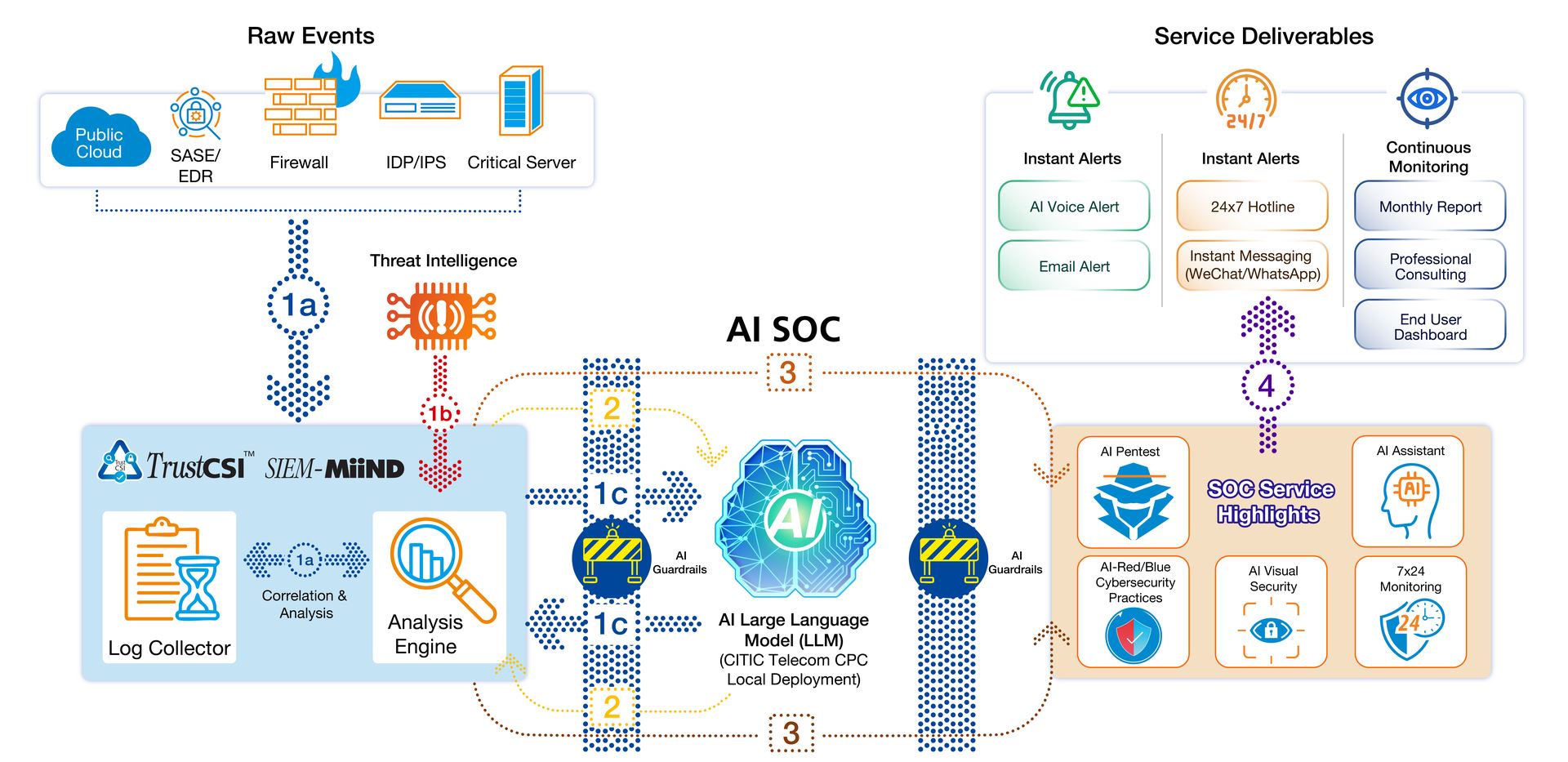
Managed Security Services: The Ultimate Security Solution for Businesses
Modern businesses face a growing number of cyber threats that can compromise their valuable digital assets. High-profile breaches continue to make headlines, and compliance requirements only add to the pressure for businesses to prioritize IT security. As a leading managed IT security service provider, CITIC Telecom CPC is committed to providing top-of-the-line security services to help safeguard businesses' cybersecurity.
CITIC Telecom CPC's TrustCSI™ MSS Managed Security Services are designed to complement 3 Security Operations Centers (SOCs) in Hong Kong, Shanghai and Guangzhou with high availability and disaster recovery functionality. With ISO27001 certified processes, we offer comprehensive and robust managed security services that include 24/7 real-time monitoring. Our services help businesses identify and analyze vulnerabilities, prioritize threats, and refine security policies and processes. By partnering with us, businesses can effectively handle the increasing demands of IT security and protect their valuable digital assets against potential security threats.
High profile breaches are on the rise. Online communities are becoming more aware and additional compliance requirements make IT security everyone’s top priority. As a managed security service provider, CITIC Telecom CPC always strives to improve security services management offerings to safeguard enterprises’ cybersecurity.
CITIC Telecom CPC’s TrustCSI™ MSS Managed Security Services, complementing multiple Security Operations Centers (SOCs) with high availability and disaster recovery functionality. Based on ISO27001 certified processes, we provide comprehensive and robust managed security services with 24 x 7 monitoring and help businesses identify and analyze vulnerabilities, prioritize threats as well as refine security policies and processes. The managed security service is designed to help you handle these increasing IT security demands effectively.