- Asia Pacific
- Hong Kong (English)
- Hong Kong (繁體中文)
- Hong Kong (简体中文)
- Japan (English)
- Malaysia (English)
- Malaysia (简体中文)
- Singapore (English)
- Singapore (简体中文)
- Europe
- English
- Estonia
- EnglishEesti
- Mainland China
- China Entercom (English)
- China Entercom (简体中文)
- Business Partner
- Tai Fu (繁體中文)
- 其他
- 产品与服务
- 信息安全管理
-
保护
网络安全设备托管服务
统一威胁管理 (UTM)托管式新世代防火墙 (NGFW)托管式网站应用程式防火墙 (WAF)网络安全安全存取服务边缘 (SASE)邮件安全邮件防护服务侦测威胁检测服务
托管式安全服务 (MSS)端点侦测及回应 (EDR)流量监控及分析用户和企业行为分析 (UEBA)网络流量分析回应及复原安全回应服务
安全编排及自动化回应 (SOAR)威胁搜捕服务安全事件回应 (IR)备份及灾难复原即服务多功能托管云备份及灾难复原解决方案 (BRR)
- 解决方案
- 技术与服务
- 关于我们
- 资源中心
- 联系我们


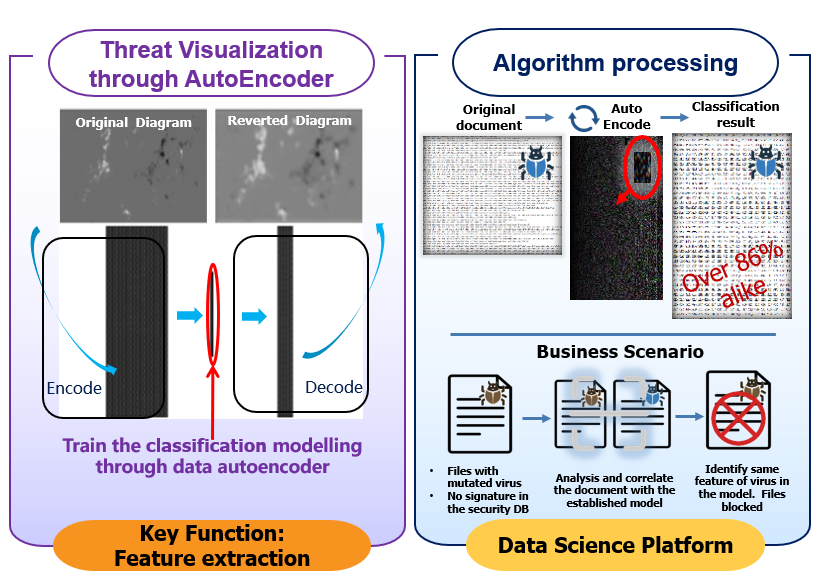
 迅速「看见」恶意软件,快速「拦截」恶意软件家族
迅速「看见」恶意软件,快速「拦截」恶意软件家族