- Products & Services
-
Europe Solutions
-
Europe to Asia / Asia to Europe
Europe & Asia West-East Global Cloud Ring
Baltic Sea
DIA PROTECT Internet Based Connectivity Solution Business Internet Solution (On-Net Tallinn) Baltic Sea Cable Estonia Data Center Solution Estonia Cloud Solution
-
TrueCONNECT™ Networking
-
MPLS (Premium)
MPLS VPN - Fully Meshed Managed Private Network
SD-WAN (Hybrid)
Redefine your Business Agility and Advantages
Secure Access Service Edge (SASE)
Cloud-native Secure WAN for Distributed Enterprise
Multi-Cloud Connect
Embrace Unlimited Possibilities to Achieve Greater Business Value
Ethernet (VPLS)
Efficient Private LAN Connectivity
MPLS Provision with IPSec Encryption (Express)
Speedy Provision Private Network with IPSec Encryption
Remote Access to MPLS (Remote)
Secure Remote Access to MPLS Private Network
Managed WAN Optimization (Accelerator)
Managed WAN Optimization Services Accelerating SPEED - Enabling BIZ
-
Information Security
-
Identify & Predict
Assessment Services
Asset Identification ServiceVulnerability Assessment ServicePenetration Test ServiceCode Review ServiceAI Visual SecurityProtect
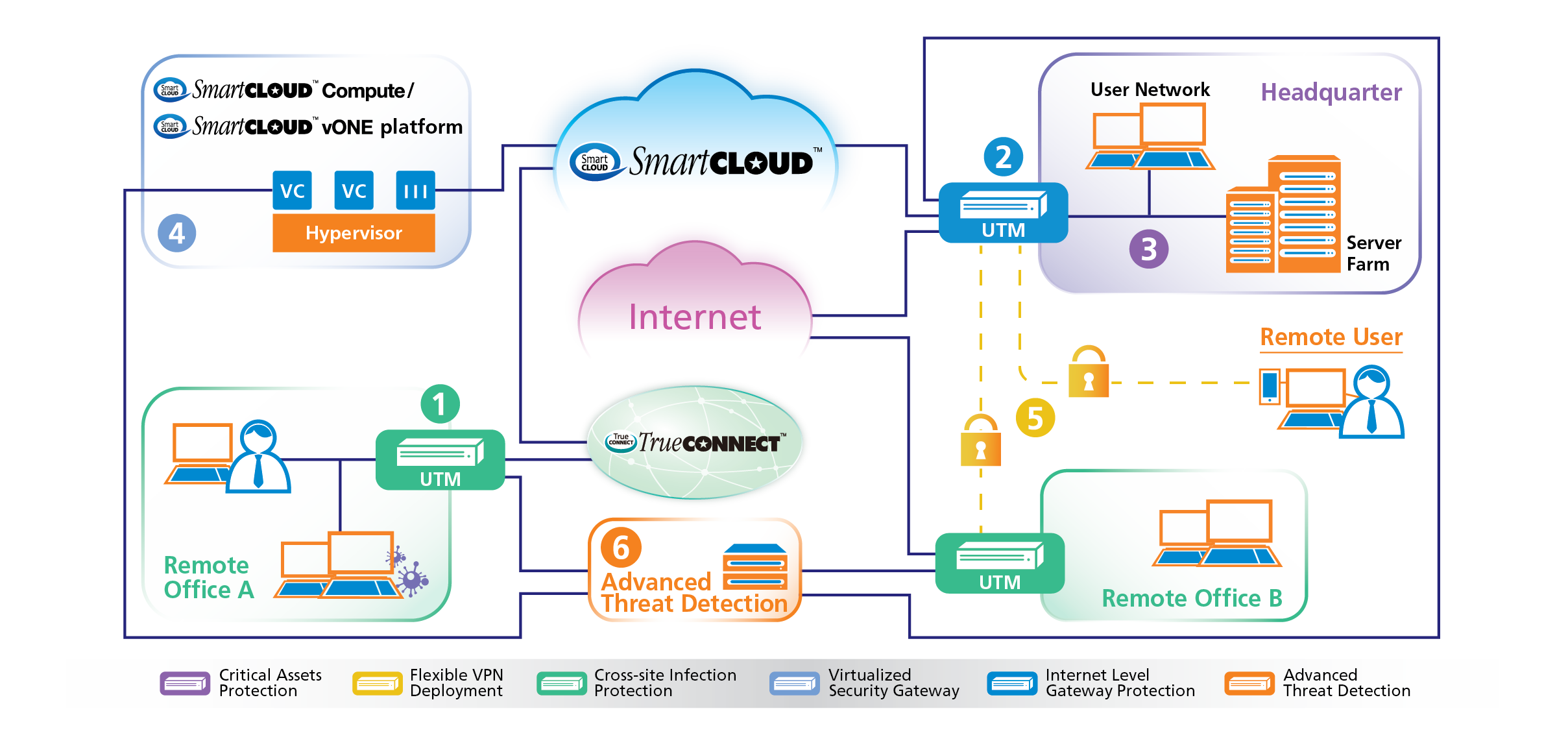
Managed Network Security Device Service
Managed Unified Threat Management (UTM)Managed Next-Generation Firewall (NGFW)Managed Web Application Firewall (WAF)Network SecuritySecure Access Service Edge (SASE)Mail SecurityMail Protection ServicesDetect
Threat Detection Services
Managed Security Services (MSS)Endpoint Detection & Response (EDR)Traffic Monitor and AnalysisSecure AI (UEBA)Network Traffic AnalysisRespond & Recover
Security Response Services
Security Orchestration, Automation and Response (SOAR)Threat Hunting ServiceSecurity Incident Response (IR)Backup & Disaster Recovery as a ServiceVersatile Managed Cloud Backup & DR Solution (BRR)SOC-as-a-Service
Professional Services & Compliance
Professional Services
Security Device Migration ServiceCloud Professional ServicesCompliance ServicesChina Cybersecurity Law MLPS 2.0 Compliance ServiceCross-Border Data Compliance Assessment Service
-
SmartCLOUD™ Cloud Solutions
-
IaaS – Infrastructure as a Service
Virtual Private Cloud (Compute) Dedicated Private Cloud (vONE)
PaaS - Platform as a Service
SaaS – Software as a Service
Secure Business Email & Collaboration (M@il) Unified Video Collaboration for Enterprise (VC)
XaaS – Anything as a Service
Versatile Managed Cloud Backup & DR Solution (BRR) Managed Object Storage (OS) Managed Virtual Desktop Service (DaaS Lite)
Professional Service
OS & Applications Management (PS) Multi-Cloud Managed Services
Cloud Connectivity
-
DataHOUSE™ Cloud Data Center
-
Global Cloud Data Centers
Reliable Environment for Your Critical Application and Data
Mainland China
Perfect Choice for Hosting and Cloud Computing
Asia Pacific
A Safe Home for Hosting Enterprise Applications and Data
Estonia Data Center Solution
DataHOUSE@Tallinn
-
Internet Services
-
Managed Services
-
DataHOUSE™ AR Remote Hand
Remote Operations and Maintenance Services
Services Management Portal (ManagedCONNECT)
One-stop Versatile Service Management Portal
Traffic Monitoring Service (TMS)
Your Reliable Network Traffic Analyser
Cloud Resources Control (Compute PA)
Resources Control and Performance Showcase
-
- Solutions
Solutions
Discover how innovative technologies and ICT solutions are transforming smart industries.
Learn more - Technology & Services
Technology & Services
Our professional teams can customize business solutions and deliver excellent customer service to support our customers’ business needs and continuous growth.
Learn moreTechnology & Services
- About Us
About Us
As an intelligent technology-driven digitalization enabler, we are committed to providing our customers with one-stop-shop ICT solutions with superior quality.
Learn more - Resources Center
Resources Center
- Contact Us
Contact Us
Contact sales to address your business needs or get help from service support.
Learn moreContact Us