Unified Threat Management for Full Protection to Cyber Security | TrustCSI™ UTM
TrustCSI™ UTM Unified Threat Management services provides enterprises a hassle-free first line network defense solution against malicious threats requires for no CAPEX investment and comprehensive technical support.
Unified Threat Management for Full Protection Enterprise Network Security
The Unified Threat Management (UTM) framework is a class of network hardware, virtual appliance, or cloud service that incorporates and integrates multiple security resources and features to protect enterprises from security threats in a simplified manner. Unified Threat Management (UTM) systems very often attract the niche as network security tools that can help protect networks from collective security threats, including malware and attacks targeting different network partitions at the same time.
For network security, Unified Threat Management (UTM) cloud services and virtual network equipment are becoming extremely popular, as with most other small and medium-sized business enterprises. Both try to eliminate the presence of on-site network security devices, yet provide centralized control and cater to the user-friendly environment to build in-depth network security. Although Unified Threat Management (UTM) solutions and firewalls of the next generation (NGFWs) are sometimes similar, Unified Threat Management (UTM) systems have additional security functions that NGFWs do not offer. Initially designed to plug the network security gaps left by conventional firewalls, NGFWs typically provide application intelligence and protection mechanisms for intrusion as well as denial-of-service prevention.
Unified Threat Management (UTM) has multiple layers of network security, namely firewalls of the next generation, intrusion detection/prevention systems, virtual private networks (VPN), antivirus, spam filtering, and web content filtering URLs.
Strong points of Unified Threat Management (UTM)
Unified Threat Management (UTM) systems usually include varying technologies for network security, which are as under:
Antispam providers block or mark incoming email attacks by scanning inbound and outbound email traffic from the Simple Mail Transfer Protocol. Browser and email antivirus scanning implies that Unified Threat Management (UTM) systems scan malware for malicious email and web application traffic.
Unified Threat Management (UTM) applications and services may also provide whitelist technologies and flag control that signify where and when applications can be of use. Application control is critical for network security, as lots of software is either malicious or contains bugs that can be used by attackers to breach network security.
The firewall is the earliest and most basic form of network security. To reduce or eliminate exposure to visible hosts, networks or protocols known to be vectors for network threats, firewalls restrict the setting up of network connections between hosts both internal and external organizational structure.
Technologies for intrusion detection and prevention identify and stop attacks by detecting when an attacker attempts to access the network and preventing the occurrence of such attacks. This type of security threat is addressed by the most effective Unified Threat Management (UTM) services through a variety of methods, including detecting malware-based attacks, deficiencies or reputation-based detection to stop both visible and invisible attack.
Unified Threat Management (UTM) often implements with virtual private network (VPN) features. While most Unified Threat Management (UTM) network security features are intended to detect and stop attacks, VPNs are explicitly designed to prevent unauthorized intrusion or prying of the network activity of an enterprise. A VPN can be configured to channelize all traffic from mobile hosts to a Unified Threat Management (UTM) device, allowing all Unified Threat Management (UTM) network security checks to get extended to mobile traffic and reducing the number of security incidents involving these gadgets.
Web content filtering and URL filtering skills cover a variety of processes that determine whether a website or URL request should or should not be allowed.
Unified Threat Management (UTM) functionalities
Unified Threat Management (UTM) systems supply increased shielding and visibility, as well as network security control, reducing intricacy. These include:
Flow-based investigation, alternatively called stream-based inspection, sample data, entering a Unified Threat Management (UTM) system and then use matching patterns to assess whether the data flow contains malicious content.
Proxy-based queries serve as a proxy to reconstruct the data entering the Unified Threat Management (UTM) system and then conduct a full inspection of the content to identify possible security threats.
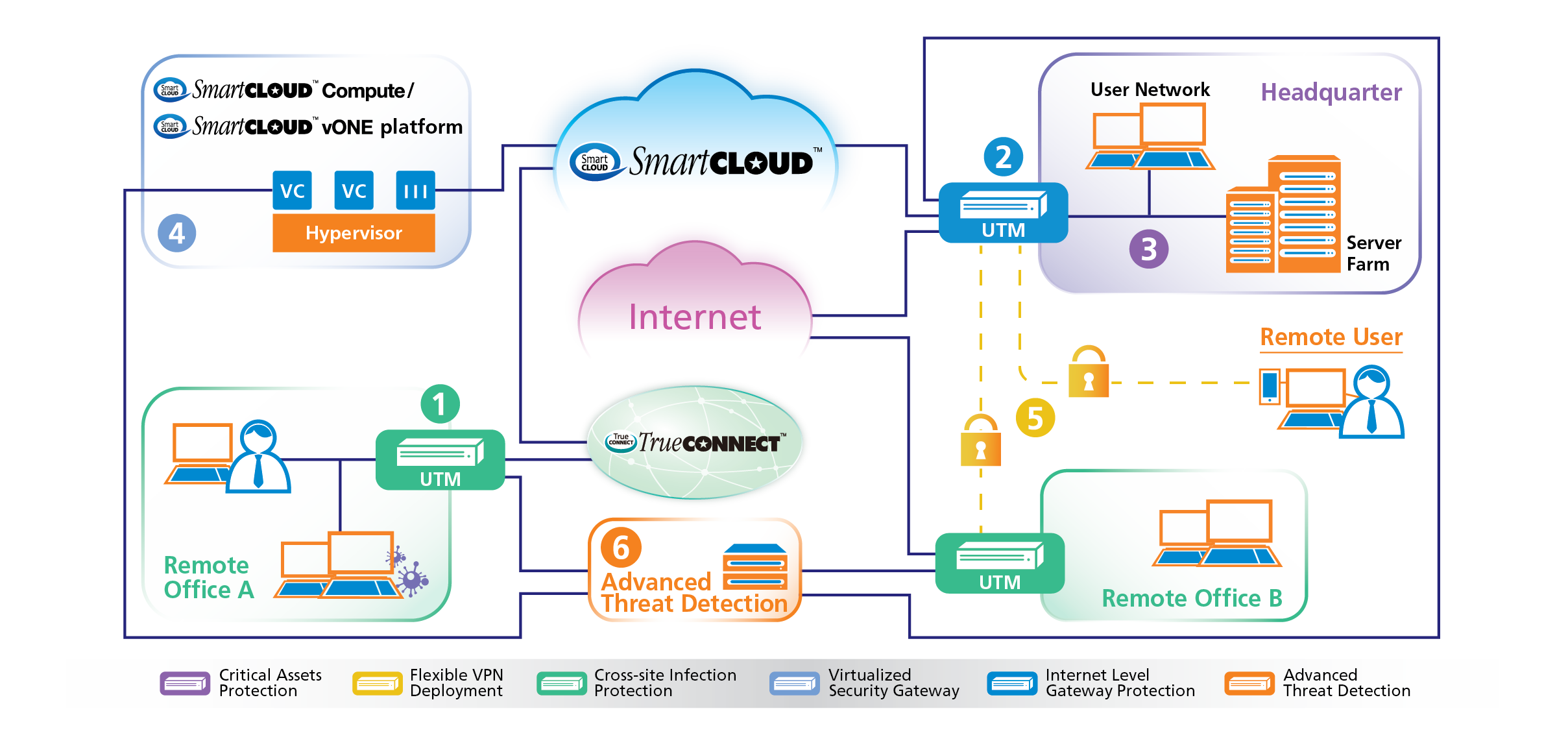
CITIC Telecom CPC’s TrustCSI™ UTM (Unified Threat Management) optimizes the smart, intuitive user interface (UI) conforming to your requirements. Our Unified Threat Management (UTM) is simple to use thanks to the configurable real-time dashboard, versatile modular licensing and intuitive network object descriptions.
As the openness of the Internet, complexities of modern businesses and the heightened interconnectivity between internal and external environment that create widespread risks for hacks, threats and vulnerabilities by sources both outside and inside a company.
Many enterprises are applying firewalls and private network as their first line defense against malicious traffic, which could merely maintain minimal protection against known threats whilst leaving the network unprotected for emerging unintended threats from insiders.
To ensure a full protection to organizations’ information security, CITIC Telecom CPC’s TrustCSI™ UTM provides enterprises a hassle-free first line network defense solution that requires for no CAPEX investment and comprehensive technical support.